OAuth: The Invisible Shield Protecting Your Digital Identity
Have you ever signed into a new app using your Google, Facebook, or LinkedInaccount and marveled at how easy it was? No long sign-up forms, no forgotten passwords, and yet — completely secure.
That convenience, that seamless experience, that invisible magic behind “Continue with Google” — all of it runs on one powerful open standard: OAuth.
In a digital era where data breaches, password fatigue, and cyber threatsare part of everyday life, OAuth has quietly become the cornerstone of online security and trust.

What is OAuth?
OAuth (Open Authorization)is an open standard for access delegation.
In simpler terms, it allows applications to access resources (like your profile data or email) on your behalf, without ever giving them your actual password.
OAuth lets users grant limited accessto their information on one site (say, Google) to another site (say, Spotify) — safely and securely.
This means:
- You log in using your existing Google or Facebook account.
- The app gets permission to use your data — but not your credentials.
- You can revoke access anytime.
Think of OAuth as a digital valet key— it allows apps to open certain doors, butnot start your entire car.
A Quick History of OAuth
- 2006:OAuth was born from a collaboration between Twitter, Google, and Blaine Cook (the developer behind Twitter’s API).
- 2010:OAuth 1.0 became a standard under the IETF (Internet Engineering Task Force).
- 2012:OAuth 2.0was released — more flexible, more secure, and widely adopted.
- Today:OAuth 2.0 powers millions of integrations across cloud services, APIs, mobile apps, and enterprise systems.
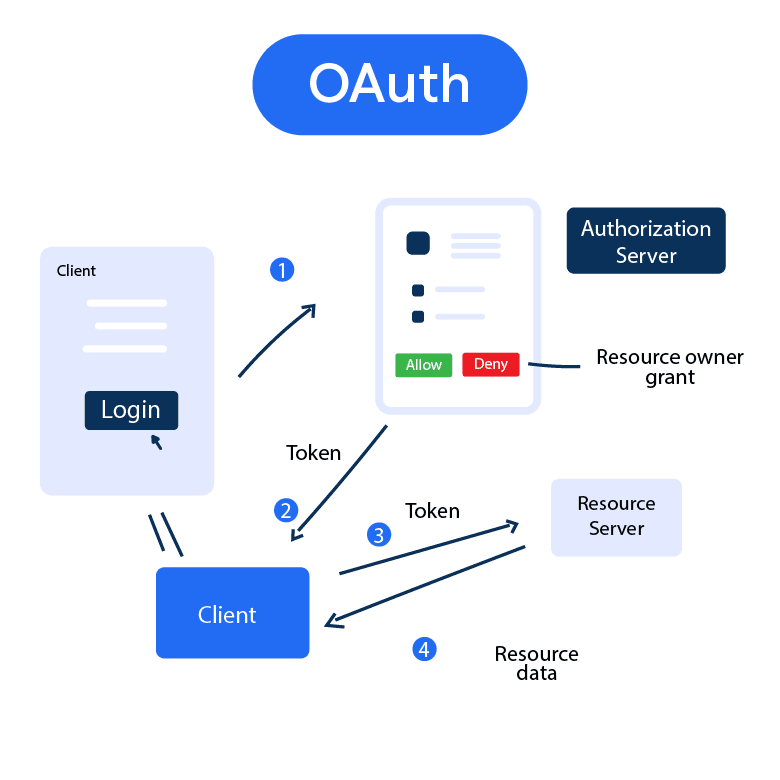
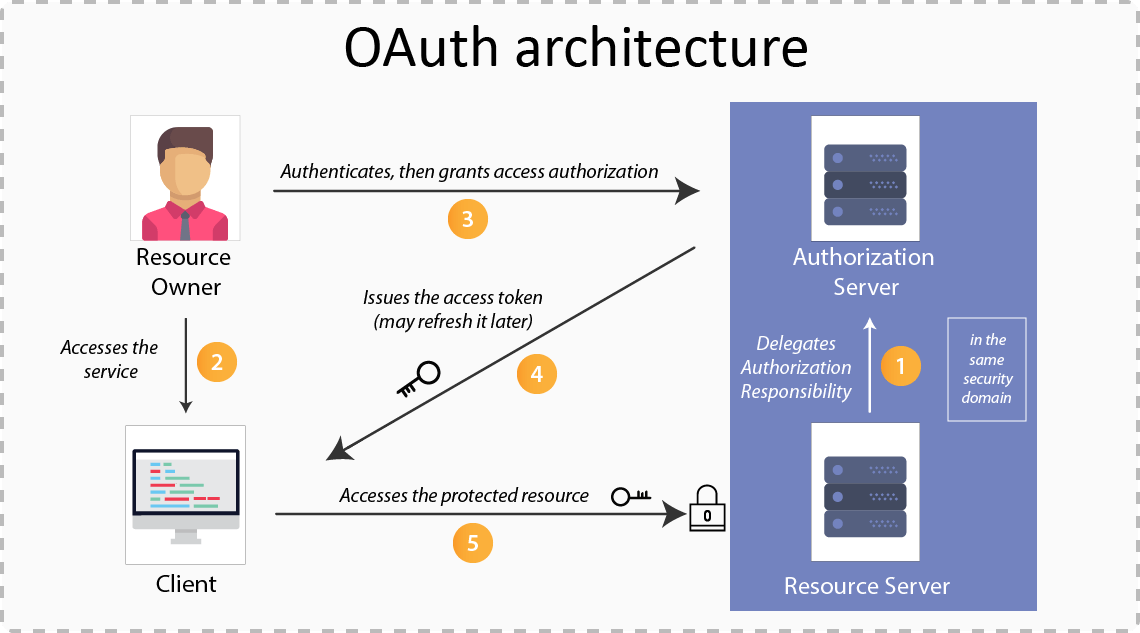
How OAuth Works?
OAuth involves four main players:
- Resource Owner:The user (you).
- Client Application:The app that wants to access your data (e.g., Spotify).
- Resource Server:The server hosting your data (e.g., Google).
- Authorization Server:The system that verifies your identity and grants access.
The Process:
- You click “Login with Google”on Spotify.
- Spotify redirects you to Google’s authorization server.
- You log into Google and grant permission.
- Google issues an access tokento Spotify.
- Spotify uses that token to fetch your name, email, or playlists from Google — without ever seeing your password.
Why OAuth Matters Today?
OAuth is the foundation of digital trustin the age of APIs and interconnected systems.
It enables secure integrationsbetween platforms while preserving user privacy— the holy grail of modern digital experiences.
From banking apps to cloud APIs, OAuth ensures that:
- You stay in control of your data.
- Businesses reduce risk exposure.
- Developers simplify authentication workflows.
Use Cases / Problem Statements Solved by OAuth
- Secure Third-Party Integrations
Problem:Apps need access to user data from other services — but asking for passwords is unsafe.
Solution:OAuth allows users to approve specific access scopes (like reading contacts or emails) securely.
Example:
When you connect a productivity app to your Gmail, OAuth enables that connection securely — without exposing your Google credentials.
- Simplified User Onboarding
Problem:Long registration forms and password fatigue reduce user engagement.
Solution:OAuth-based “Sign in with Google/Facebook” reduces friction and improves conversion rates.
Example:
E-commerce platforms like Shopify or SaaS tools like Notion use OAuth to offer quick sign-in options.
- Enterprise API Access Control
Problem:Organizations struggle to manage API access securely across teams and applications.
Solution:OAuth provides fine-grained, token-based accesscontrol for APIs — perfect for enterprise environments.
- Mobile and IoT Authentication
Problem:Devices and mobile apps need secure access tokens instead of storing passwords.
Solution:OAuth allows mobile apps and IoT devices to use short-lived tokens, minimizing security risks.
- Data Privacy and Compliance
Problem:With regulations like GDPR, data sharing must be consent-based and auditable.
Solution:OAuth inherently supports explicit consentand scope-based access, ensuring compliance.
Pros of OAuth
| Advantage | Description |
| Enhanced Security | No passwords are shared between apps — reducing breach risk. |
| Better User Experience | Users can log in with existing accounts instantly. |
| Granular Access Control | Tokens specify exactlywhat data an app can access. |
| Revocable Permissions | Users can revoke app access anytime. |
| API-Friendly | Ideal for modern API ecosystems and microservices. |
| Multi-Platform Support | Works seamlessly across web, mobile, and IoT. |
Limitations of OAuth
While OAuth is powerful, it’s not without challenges.
- Implementation Complexity:
Getting OAuth right requires deep understanding of flows, scopes, and tokens. A small misconfiguration can create security loopholes.
- Token Misuse Risks:
Access tokens can be stolen if not handled securely.
- No Built-in Authentication:
OAuth itself doesn’t authenticate users — it delegates authorization. You often need OpenID Connect (OIDC)for identity management.
- Multiple Flows, More Confusion:
OAuth 2.0 offers several “flows” (authorization code, implicit, client credentials, etc.), which can overwhelm beginners.
- Dependency on Authorization Servers:
If your authorization provider (like Google) goes down, connected apps lose access temporarily.
Alternatives to OAuth
| Alternative | Description | When to Use |
| OpenID Connect (OIDC) | An authentication layer built on top of OAuth 2.0. | When you need both authentication and authorization. |
| SAML (Security Assertion Markup Language) | XML-based single sign-on protocol. | Common in enterprise identity systems. |
| JWT (JSON Web Tokens) | Token-based authentication mechanism. | Lightweight authentication between services. |
| API Keys | Simple static credentials for API access. | Small-scale projects with limited security needs. |
| Basic Auth | Username-password authentication. | For internal or testing environments only. |
Upcoming Updates / Industry Insights
Upcoming Updates / Industry Insightsof OAuth
The OAuth 2.1specification (currently in progress) is the next evolution of OAuth 2.0 — consolidatingbest practices and eliminatingdeprecated flows.
What’s Coming:
- Simplified documentation.
- Stronger token handling practices.
- Removal of outdated implicit flow.
- Improved security around PKCE (Proof Key for Code Exchange).
Industry Trends:
- Zero Trust Architectures:OAuth plays a key role in implementing Zero Trust models where every request is authenticated and authorized.
- API Economy Growth:As APIs become the backbone of digital ecosystems, OAuth ensures safe, scalable access.
- Identity Federation:OAuth underpins single sign-on (SSO) and multi-cloud authentication strategies globally.
Project References
Frequently Asked Questions on OAuth
Q1. Is OAuth the same as OpenID Connect?
No. OAuth handles authorization (granting access), while OpenID Connect adds authentication (verifying identity).
Q2. Can OAuth be used without HTTPS?
Technically yes, but it’s highly discouraged. Tokens transmitted over plain HTTP can be intercepted.
Q3. What is an access token in OAuth?
A short-lived credential used by an app to access protected resources on behalf of a user.
Q4. How is OAuth different from API keys?
API keys are static and tied to an app; OAuth tokens are dynamic, user-specific, and revocable.
Q5. Is OAuth secure?
When implemented correctly, OAuth is among the most secure authorization frameworks available.
Third Eye Data’s Take on OAuth
We treat OAuth(and similar identity / authorization protocols) as a foundational security layer in our AI application deployments. At Third Eye Data, we integrate OAuth (or equivalents like OpenID Connect) in our authentication flows, API gateways, and user access systems to enable secure, role-based access across data and AI services. Though not always named publicly, it’s part of our security architecture under the hood.
In a world that runs on interconnected applications and cloud APIs, OAuth is the silent hero of digital trust. It ensures that your data stays private, your passwords remain confidential, and your digital experiences remain frictionless.
For developers, OAuth brings a unified, secure, and user-friendlyway to connect systems.
For businesses, it ensures compliance, scalability, and customer trust.
And for users, it represents control, convenience, and confidence.
As the world moves toward decentralized identity, Zero Trust security, and cross-platform integration, OAuth will continue to evolve — remaining at the heart of how we authenticate and authorize online.
Whether you’re:
- Building a new SaaS product
- Developing a mobile app
- Managing enterprise APIs
Implementing OAuth is your first step toward a secure and seamless user experience.
Ready to make your app OAuth-powered?
Our cloud and security experts can help you:
- Integrate OAuth 2.0 and OpenID Connect
- Implement token-based access for your APIs
- Ensure compliance with the latest security standards
Get in touch todayto future-proof your authentication and safeguard your users.