Microsoft Sentinel: Taming the Chaos of Modern Cyber Threats
The Security Nightmare is Over
The modern digital world is a sprawling, chaotic city. Your assets—data, applications, identities—are scattered across skyscrapers (Azure), competitor blocks (AWS/GCP), and historical neighborhoods (on-premises servers). Meanwhile, the threats aren’t simple smash-and-grabs; they are sophisticated, distributed heists targeting multiple points at once.
If your Security Operations Center (SOC) is still relying on traditional, legacy SIEMs (Security Information and Event Management), it’s like trying to patrol this sprawling metropolis with a single watchman and a paper map. They are slow, limited by physical hardware, and can’t see the big picture.
Microsoft Sentinelis here to change the game.
Sentinel is the ultimate, cloud-native SIEM and SOAR (Security Orchestration, Automation, and Response)platform. Built entirely on Azure, it is the central command center that gives you superhuman vision, AI-driven intelligence, and the power to automaticallyneutralize threats at cloud scale.
It doesn’t just collect logs; it ingests massive volumes of security datafrom every corner of your estate—endpoints, clouds, apps, networks, IoT—and uses AI and Microsoft’s global threat intelligenceto connect the dots, find the hidden threats, and automate the precise response.
Unlike those infrastructure-heavy, “lift-and-shift” SIEMs, Sentinel is elastic, intelligent, and natively integrated, ensuring your defense posture is always one step ahead.

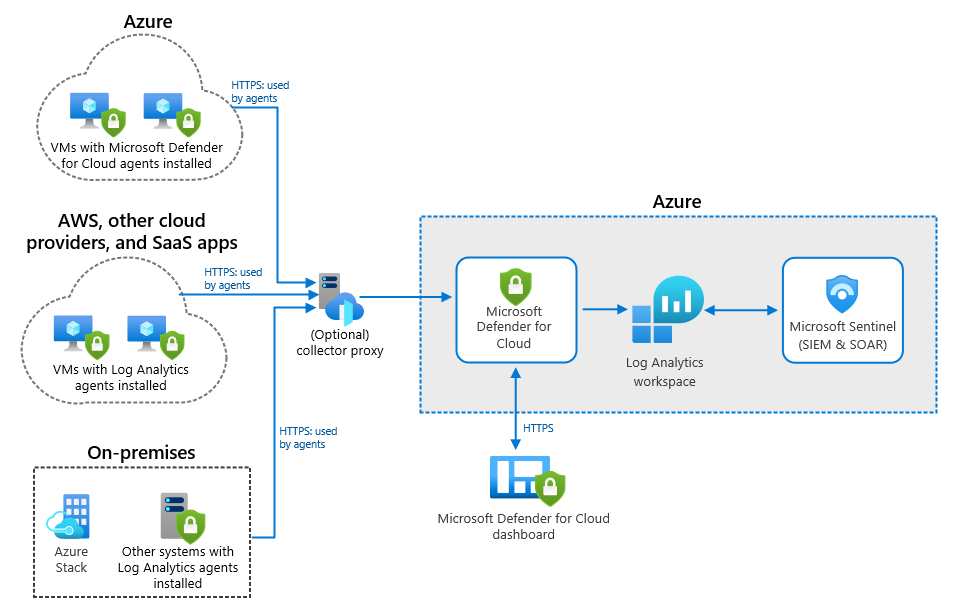
Hybrid-Security-Monitoring-with-Microsoft-Sentinel
Image Courtesy: microsoft.com
Sentinel: Solving the Defender’s Core Dilemmas
Sentinel doesn’t just manage logs; it solves the problems that keep security teams awake at night:
- The Unified “Big Picture” (Unified Threat Visibility):Your environment is fragmented (Azure, AWS, M365, Cisco, Palo Alto). Sentinel acts as the single aggregator, pulling telemetry from all these sources into one 360° view. No more bouncing between siloed tools to find the trail.
- Finding Needles in Haystacks (Intelligent Threat Detection):Attackers are quiet and fast. Sentinel uses Machine Learning analyticsand the intelligence from the Microsoft Security Graph(monitoring trillions of signals daily) to spot subtle anomalies—like suspicious lateral movements or privilege escalations—beforethey become full-blown breaches.
- Fighting Fire with Automation (Automated Incident Response):Analysts are overwhelmed by noise. Sentinel uses SOAR playbooks (powered by Azure Logic Apps)to automate repetitive tasks: isolating an infected endpoint, disabling a compromised account, or blocking a malicious IP. This drastically reduces the MTTR (Mean Time to Resolution), letting human experts focus on strategic analysis.
- The Compliance Safety Net:It centralizes log storage and provides real-time auditing dashboards (GDPR, HIPAA, ISO 27001), turning audit season from a stressful scramble into a simple reporting task.
- The Wolf in Sheep’s Clothing (Insider Threat Detection):Machine learning models analyze behavioral patterns across your systems to identify unusual logins or data access, pinpointing a compromised identity or a malicious insider.
- The Multi-Cloud Referee:Whether you use Azure, AWS, Google Cloud, or your own data center, Sentinel provides the single pane of glassto monitor the security of all of them simultaneously.
The Sentinel Superpowers
| Feature | Technical Benefit | Human Translation |
| Cloud-Native Elasticity | Built entirely on Azure; scales automatically without server or storage provisioning. | Unlimited growth potential; your SIEM capacity is never the bottleneck. |
| AI-Driven & Intelligent | Leverages Microsoft’s global threat intelligence and ML to detect threats and reduce false positives. | You get the collective security knowledge of Microsoft’s entire global defense team baked into your system. |
| Microsoft Ecosystem Native | Integrates natively and deeply with Azure AD, Microsoft Defender, and Microsoft 365. | Frictionless, end-to-end visibility across your most critical environments. |
| Built-In SOAR | Uses Azure Logic Apps to create auto-remediation workflows. | Your SOC goes from manual firefighting to automated, rapid response—making analysts more effective. |
| Open and Extensible | Supports 100+ pre-built connectors (Cisco, Palo Alto, AWS CloudTrail) and custom data via Log Analytics API. | You don’t have to rip and replace existing security tools; Sentinel plays well with everyone. |
| Pay-As-You-Go Model | Pricing based on data ingested, not rigid license tiers or hardware costs. | Cost-efficient and transparent—you only pay for the security value you consume. |
| Actionable Visuals (Workbooks) | Powerful dashboards built on Azure Monitor and Kusto Query Language (KQL). | Insights, not just data. Security leadership gets clear, actionable intelligence instantly. |
The Defender’s Disclaimers (Things to Know)
- The KQL Learning Curve:To truly unlock Sentinel’s analytic power—writing custom rules and dashboards—your analysts must become fluent in the Kusto Query Language (KQL). It’s a skill investment, but one with massive payoff.
- Data Volume Cost Risk:While pay-as-you-go is great, allowing every single log source to stream in without optimization can lead to unexpectedly high costs. Data ingestion optimizationand smart retention policies are critical.
- Cloud-Native Limitation:Being a cloud-native platform means it relies on stable internet connectivity. It’s not the ideal solution for environments that must be fully air-gappedfrom the public internet.
The Competition: Who Else Is On The Field?
Sentinel isn’t the only player. Here’s how it stacks up against the major league alternatives, helping you choose the right tool for your specific environment:
| Platform | Type | The Sales Pitch (Key Strengths) | The Technical Catch (Trade-offs) |
| Splunk Enterprise Security | On-Prem/Cloud | Deepest analytics, massive partner ecosystem, widely adopted. | Expensive(often license-based), and if self-hosted, it’s infrastructure-heavyand requires constant patching/upgrades. |
| IBM QRadar | On-Prem/Cloud | Excellent for advanced, complex correlation rules and long history of enterprise trust. | Can be a complex deploymentand often requires specialized skill sets to manage and tune effectively. |
| Elastic Security (ELK Stack) | Open Source | Highly flexible, customizable, and has a great free tier. | The “free” aspect is misleading; it requires a high maintenance effortand significant internal engineering expertise to scale and secure. |
| Google Chronicle | Cloud | Incredible speedand Google-scale analyticsfor petabytes of data ingestion. | Fewer built-in SOAR/automation optionscompared to Sentinel, requiring more integration work. |
| Securonix | Cloud | Very strong focus on UEBA (User and Entity Behavior Analytics)and behavioral threat detection. | Can become higher cost at scalethan Sentinel if data volumes are not carefully managed. |
The Future is Now: Sentinel’s Next Evolutions
The speed of innovation in Sentinel is staggering, with a heavy focus on AI and XDR:
- Security Copilot Integration:Prepare for the next wave. Microsoft is baking GPT-based reasoninginto Sentinel, giving analysts an AI co-pilotfor instant investigation summaries, guided threat hunting, and automated action suggestions.
- Defender XDR Control Plane:Sentinel is evolving into the unified control center for all Microsoft Defender products (Endpoint, Cloud, Identity), creating a seamless, end-to-end Extended Detection and Response (XDR)experience.
- Cost-Efficient Archiving:New long-term data archive options are rolling out, allowing you to store petabytes of historical data for compliance or forensic analysis at a significantly lower cost.
Frequently Asked Questions about Microsoft Sentinel
Q1: How is Microsoft Sentinel different from Azure Security Center?
Azure Security Center provides cloud security posture management (CSPM), while Sentinel is a full SIEM/SOAR platform for log analytics, correlation, and automated response.
Q2: Can Microsoft Sentinel monitor non-Microsoft platforms?
Yes. Sentinel supports over 100 connectors for AWS, GCP, Cisco, Palo Alto, Okta, and many other third-party vendors.
Q3: What is KQL and why is it important in Sentinel?
Kusto Query Language (KQL) is used to query logs in Azure Monitor. It’s essential for writing analytics rules, dashboards, and alerts.
Q4: How does Sentinel integrate with automation tools?
Sentinel uses Azure Logic Apps for automation, allowing you to create playbooks for auto-remediation, notifications, or ticketing system integration.
Q5: Is Sentinel suitable for small and medium businesses?
Yes. Sentinel’s pay-as-you-go model and low infrastructure requirements make it cost-effective for organizations of all sizes.
ThirdEye Data’s Take: The Modern SOC Cornerstone
At ThirdEye Data, we consider Microsoft Sentinel to be the most crucial SIEM + SOAR platformfor any forward-thinking enterprise today.
It resolves the decades-old conflict between scalability, automation, and intelligence.Its cloud foundation, combined with the unparalleled power of Microsoft’s threat research, transforms traditional, reactive SOCs into proactive, intelligent security hubs.
For organizations navigating the complexity of hybrid and multi-cloud environments, Sentinel doesn’t just meet the current security standard—it sets the new benchmark.
ThirdEye Data recommends Microsoft Sentinel as the cornerstone of a next-generation cybersecurity strategy. It is the platform that not only detects threats faster than humanly possible but learns, adapts, and neutralizes them automatically, securing your future in the cloud.
