Cloud-Native, Scalable, Role-Based IAM: The Backbone of Secure Modern Systems
Your team has just launched a new microservices platform for your product — several services talk to each other, access sensitive data, and users authenticate via your identity provider. One day, someone accidentally gives “admin” privileges to a junior developer. That developer’s account is compromised, and suddenly critical functions are being altered, data exfiltrated, billing abused. It takes days to audit logs, roll back, and re-secure.
That’s why Identity & Access Management (IAM) is not just security hygiene — it’s vital infrastructure. But as systems evolve (from monoliths to microservices to serverless), IAM must evolve too. The new paradigm is cloud-native, scalable, and role-based IAM.
In this post, I’ll walk you through how modern IAM is built, why role-based cloud-native IAM matters, how it connects through your infrastructure, its strengths and pitfalls, what’s emerging next, and how you can implement it in your architecture. Think of this as your deep dive into the guardrails behind modern platforms.

What Is Cloud-Native, Scalable, Role-Based IAM?
Let’s break down the phrase:
- Cloud-native: Designed to work inherently in cloud environments — API-driven, managed, resilient, multi-tenant, and integrated with cloud infrastructure components.
- Scalable: Capable of handling growth — thousands or millions of identities, permissions, services — without manual scaling or bottlenecks.
- Role-based: Instead of individually assigning permissions to users, you group permissions into roles (or role hierarchies) and assign those roles to identities (users, service accounts, applications, etc.).
Putting it all together: Cloud-native, scalable, role-based IAM is a system or layer in modern cloud platforms (AWS IAM, Google Cloud IAM, Azure AD, or custom IAM systems) that allows you to define roles, attach permissions, manage identities, and enforce access control across all components in a scalable, manageable, and secure way.
In such systems:
- Permissions are defined at a granular, scoped level (e.g. “read access to bucket X”, “invoke service Y”).
- Roles compose sets of those permissions (e.g. “analytics_role”, “data_reader”, “admin_service_role”).
- Identities (users, services, groups) are assigned roles as needed.
- Policies may allow fine-grained overrides, constraints (time of day, source IP, conditional access).
- The IAM layer is declarative and policy-driven, often integrated with infrastructure-as-code and CI/CD.
- It must integrate across all services (compute, storage, APIs, serverless, microservices, custom services).
In cloud-native architecture, IAM is not a bolt-on — it’s woven throughout your system: APIs, services, event pipelines, UI front ends, microservices, etc.
Use Cases / Problem Statements Solved with Role-Based Cloud-Native IAM
Here are real problems modern systems face — and how this IAM approach helps solve them.
Use Case 1: Microservices & API Security
In a microservices architecture, ServiceA needs to call ServiceB, but only certain endpoints. You can’t hardcode credentials or open permissive access. Instead:
- Assign ServiceA a “role_serviceA_callers” role that grants minimal API scopes to ServiceB.
- If ServiceA’s instance is compromised, its access is limited to what the role allows — not full system access.
This principle of “least privilege via IAM roles” is essential in distributed systems.
Use Case 2: Multi-Tenant SaaS Platforms
You build a SaaS product serving multiple customers. Each customer should see only their own data, and operations staff have limited, role-based access for debugging.
- Use IAM to define roles like customer_admin, customer_readonly, support_engineer.
- When support engineers assist, they assume ephemeral roles bound to customer scopes (Just-In-Time access).
- Audit and logging are tied to identity/role context to maintain traceability.
Cloud-native IAM makes it possible to enforce tenant boundaries at every API or database access layer.
Use Case 3: DevOps & Infrastructure Permissions
Teams need access to infrastructure — deploy pipelines, update configurations, manage services — but you don’t want to give all-encompassing “owner” access.
- Define roles like deployment_role, monitoring_viewer, infra_admin.
- Use policy conditions (e.g. only from CI environment, only during maintenance windows).
- Integrate IAM with Infrastructure-as-Code (IaC) so that permissions are versioned, audited, and reproducible.
This ensures safe, auditable, and scalable operations practices.
Use Case 4: Fine-Grained Data Access Governance
Modern data systems often have granular data zones (e.g. customer PII, analytics, redacted data). You need:
- Roles tied to data sets or columns (via row-level security, view permissions).
- Conditional policies (only allow data access from certain contexts).
- Ability to change demarcations over time.
Role-based IAM tied to data services (BigQuery, databases) can enforce those access boundaries consistently.
Use Case 5: Temporary / Just-In-Time Access & Role Elevation
Long-lived admin roles are dangerous. Instead:
- Use IAM to grant temporary elevated roles (e.g. must request via ticketing).
- Role elevation may be time-limited, logged, and automatically revoked.
- This reduces exposure from forgotten credentials or unnecessary privilege.
Role-based IAM with conditional logic supports JIT access models.
Problem Statements Commonly Addressed
- “Our dev teams have full access, and whenever someone leaves, we can’t audit or revoke permissions easily.”
- “Service accounts from one environment are leaking data to another.”
- “Permissions are scattered, ad hoc, and inconsistent.”
- “We have microservices calling each other — how do we enforce which can call what?”
- “We need least privilege, but manual permission management doesn’t scale.”
- “We want to audit who did what, when, with which role context.”
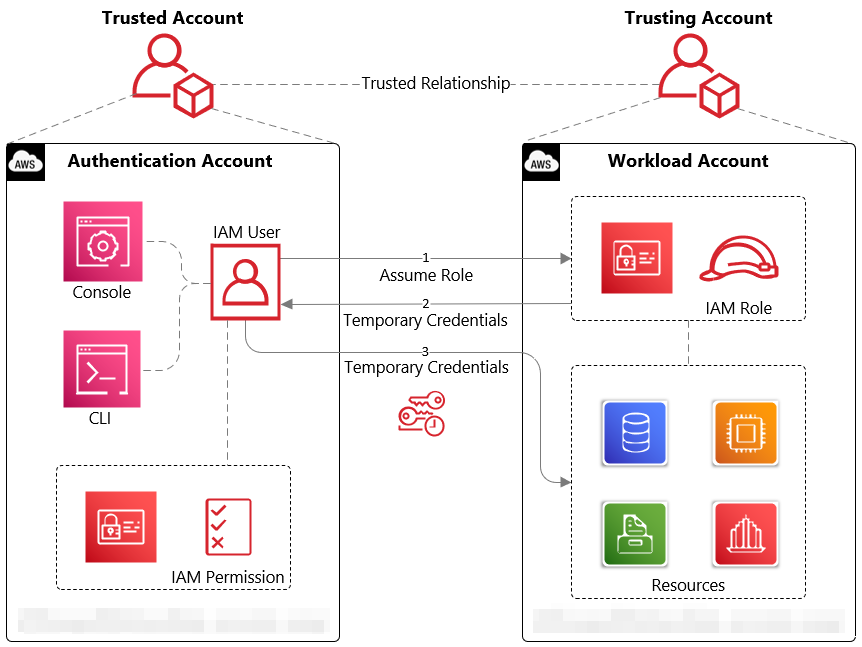
How the Components Are Connected (Architecture and Flow)
Understanding how role-based IAM flows through a cloud-native stack helps you see where to enforce controls. Here’s a typical architecture and connection flow:
[User / Client]
│ Auth (login, MFA) → Identity Provider (IdP)
▼
[Token / Credentials issued (JWT, Access Token)]
│ Contains assigned roles, claims
▼
[API Gateway / Front-end Microservice]
│ Validates token, extracts role claims
│ Checks policy: is role allowed to call this API?
▼
[Business Microservices / Backend Services]
│ Internal service-to-service calls – use IAM role tokens or service identities
│ Enforce role-based checks (RBAC) at API method level
▼
[Data Layer / Resource Access]
│ IAM roles control who can access which database, buckets, queues
│ Role-based ACLs linked to roles in IAM
▼
[Logging / Audit / Monitoring]
│ Every action is logged with identity + role context
│ Auditing and review use these logs to ensure compliance
Let’s break it down further:
- Identity Source / Identity Provider
Users authenticate (via SSO, OAuth, OIDC) to your central IdP (such as Auth0, Google Identity Platform, AWS IAM, Azure AD). That IdP issues tokens (JWT or access tokens) with role claims.
- Role Assignments / Role Management
Administrators define roles and assign them to identities (users, groups, service accounts). Roles have attached permissions (scopes). This is configured declaratively (via UI or IaC).
- Token Issuance / Claims
When users or services authenticate, they receive tokens containing role claims, context, and condition data.
- Enforcement at Entry Points (Gateways / API Layer)
API gateways or entry services validate tokens and enforce policies: i.e. check whether the role is permitted to call an endpoint (via routing rules).
- Internal Enforcement in Services
Each service, on receiving a request, introspects the role from the token and applies logic-level checks (e.g. if role == “read_only” then deny write`).
- Data / Resource Access Control
At the resource level (databases, file storage, queues), IAM roles control which roles can access which resources (e.g. provide storage.objects.get only to roles having that permission).
- Conditional / Contextual Policies
Role-based policies may have conditions (time, IP, MFA, environment, resource tags) to limit when or where privileges apply.
- Logging / Auditing / Reporting
Every API call, authorization decision, role assumption is logged with identity + role context for audits, security reviews, compliance.
- Governance, Role Evolution, Versioning
As systems grow, roles evolve. With versioned role definitions (IaC), change reviews, and audit logs, you maintain governance over the IAM structure.
In modern cloud environments, IAM is everywhere — in service mesh, K8s, serverless, custom services, data platforms. Role-based IAM is the shared security fabric across this heterogeneous landscape.
Strengths & Benefits Cloud-Native, Scalable, Role-Based IAM
Why cloud-native, scalable, role-based IAM is essential for any mature system:
- Least Privilege & Security Boundaries
Roles enforce least privilege — you don’t grant more rights than necessary. If a compromised component or identity exists, damage is limited.
- Scalability & Manageability
Assign permissions to roles (not individual users) — changes propagate, management is easier at scale.
- Separation of Concerns & Infrastructure Integration
The IAM layer is distinct from business logic — you centralize security rather than distributing ad hoc checks.
- Consistent Enforcement Across Services
The same role definitions and policies apply across microservices, APIs, data stores, serverless functions.
- Auditing & Traceability
Roles give context to actions (which identity, which role, which permission was used), which is crucial for security reviews.
- Conditional / Contextual Access Support
You can build sophisticated policies (e.g. only allow write from corporate IPs, or only during business hours).
- Declarative & Infrastructure-As-Code Friendly
Role definitions and policies are codified (YAML, JSON, Terraform) and versioned, enabling peer review, rollback, and compliance.
- Better DevOps / Principle of Least Access for Services
Service accounts (microservices) also have roles — no more “overprivileged” service tokens.
- Flexibility for Just-In-Time / Temporary Elevation
Teams can be granted elevated access only when needed, tied to duration or policy triggers.
- Strong Integration with Cloud Platforms
Cloud providers (GCP, AWS, Azure) provide native IAM systems — role-based IAM is foundational to integrating with resources (Compute, Storage, APIs).
Trade-Offs & Challenges of Cloud-Native, Scalable, Role-Based IAM
Role-based IAM is powerful, but it has trade-offs. Mistakes or oversights can be costly.
- Complex Role Design & Role Explosion
If you create too many roles or overly granular roles, management becomes burdensome (role explosion).
- Overprivilege via Poor Role Design
Roles often accumulate permissions over time (“permission creep”) — people add “just in case” privileges, eroding security.
- Conditional Policies Complexity
Policies with conditions (e.g. time-of-day, resource tags) are easier to make mistakes, causing unexpected refusal or unintended permission leaks.
- Token Size / Identity Overhead
Embedding many roles/claims in tokens can increase token size and parsing overhead.
- Latency / Token Refresh Issues
Role changes (revocations) may not take immediate effect if tokens are cached or long-lived.
- Lack of Context in Role Assignment
Some systems only consider roles per identity, not the context (which project, which tenant), leading to cross-tenant leaks if not carefully designed.
- Migration & Refactoring Difficulty
Evolving role structures (merging, splitting roles) can require complex migration of assignments and careful cutovers.
- Vendor Lock-In / Platform-Specific Constructs
Deep integration with cloud IAM systems makes portability harder. Rewriting IAM or migrating to another platform can be painful.
- Blind Spots in Custom Services
If you build custom microservices or legacy systems outside IAM enforcement, gaps can emerge where role checks are bypassed.
- Role Assignment Governance & Audit Overhead
You need processes to review role assignment, enforce separation of duties, periodic audits — otherwise, roles become outdated or insecure.
Alternatives & Complementary Approaches of Cloud-Native, Scalable, Role-Based IAM
Role-based, cloud-native IAM is not the only security model. Depending on needs, you may complement or replace it partially:
- Attribute-Based Access Control (ABAC)
Instead of roles, permissions are granted based on attributes (user attributes, resource attributes, context). More flexible but more complex.
- Policy-Based Access Control (PBAC) / Policy-as-Code
Policies define access via rules, not roles — e.g. OPA (Open Policy Agent) style. This can provide dynamic access logic beyond simple role models.
- ACLs / Rights-based Access on Resources
Traditional access control lists (resource-level permissions) — logic is embedded in each resource rather than centralized IAM.
- Capability-Based Security
Instead of roles, entities hold tokens (capabilities) that permit operations — more fine-grained delegation models.
- Zero-Trust / Contextual Access Models
Combine IAM with real-time signals (device health, risk scoring, SSO context) to enforce access, going beyond static roles.
- Service Mesh / Sidecar Authorization
Using service mesh (Istio, Linkerd) with sidecars to enforce authorization policies between services (can complement IAM).
- Hybrid Models
Many systems blend role-based IAM with policy-based decision layers for specific microservices or cross-cutting logic.
Upcoming Updates / Trends & Industry Insights of Cloud-Native, Scalable, Role-Based IAM
Here’s what’s shaping the future of cloud-native, scalable, role-based IAM:
- Fine-Grained Policy Engines & Attribute-Based Access (ABAC + PBAC)
Many IAM systems are evolving to support richer logic (attributes, contextual policies) beyond basic roles.
- Just-In-Time (JIT) / Temporary Role Elevation
Platforms are increasingly supporting ephemeral role elevation (via ticketing or approval) — reducing standing privileges.
- Decentralized Identity & Self-Sovereign Identity (SSI)
With standards like DID, verifiable credentials may change how identities and roles are provisioned and managed.
- Integrated IAM + Service Mesh / API Gateways
Closer coupling between IAM and runtime enforcement (sidecars, API gateways) ensures role checks closer to execution.
- AI/ML-Based Role Recommendations & Governance
Systems can analyze usage patterns and suggest role cleanup, detect overprivileged roles, or optimize permission sets automatically.
- Cross-Cloud / Multi-Cloud IAM Portability
Organizations use multiple clouds — IAM systems are evolving to allow role definitions and policies to be portable across environments.
- Decayed / Time-Limited Roles & Credential Lifetimes
By default, roles expire or require renewal, reducing risk of stale/abandoned privileged accounts.
- Continuous / Risk-Based Access Scoring
Instead of static roles, dynamic risk scores or context can adjust privilege levels in real time.
- Standardization & Policy Interchange Formats
Efforts like XACML, ALFA, or open policy specification formats help make role & policy definitions portable.
- Better Developer Tooling & IAM Observability
Role impact simulation, role change analysis, IAM diff tools, and dashboards to understand access surfaces will improve.
These trends show that role-based IAM is not static — it’s evolving to become more flexible, dynamic, and context-aware while maintaining scalability and manageability.
Project References & Real-World Examples of Cloud-Native, Scalable, Role-Based IAM
Frequently Asked Questions on Cloud-Native, Scalable, Role-Based IAM
Q1: Why use roles instead of giving direct permissions to users?
Roles simplify management: you update role definitions rather than individual users. They scale much better and reduce errors.
Q2: What is IAM “role hierarchy”?
A structure where roles can include or inherit other roles (e.g. admin includes read_only + write_access). But hierarchies must be used carefully to avoid explosion of implied permissions.
Q3: How do conditional roles work?
Some IAM systems support conditions (if user is in location X, time between Y, IP allowed). Roles may have constraints — only active under certain conditions.
Q4: How do you handle role revocation immediately?
Short-lived tokens, forcing refresh, or revocation notifications help ensure role changes take effect quickly.
Q5: Can a service account assume multiple roles?
Yes — identities can hold multiple roles; but overlapping roles can lead to confusing privilege surfaces if not managed carefully.
Q6: How do you audit role usage or detect privilege creep?
Use logs: record which principal used which role for which action. Use analytics to find rarely-used roles or permissions, and prune accordingly.
Q7: How do I migrate from a monolithic IAM model to role-based IAM?
Start with a small reference domain (e.g. a set of services), define roles, migrate identities there, and gradually expand. Use permission inheritance, audit testing, and fallback paths.
Q8: Is role-based IAM sufficient for all security needs?
Not always. For very fine-grained logic (e.g. business rule conditions), you may need policy-based or contextual logic layered over roles.
Third Eye Data’s Take on Cloud-Native, Scalable, Role-Based IAM
We believe cloud-native, scalable, role-based IAM (Identity and Access Management) is non-negotiable in enterprise AI systems. Scalability demands microservices, auto-scaling clusters, and secure API gateways. Role-based IAM ensures data and features are only visible by authorized users, which is crucial for trust, compliance, and auditability. At Third Eye Data, we integrate IAM systems with our AI platforms—often using cloud IAM (Azure AD, GCP IAM, AWS IAM) plus custom access controls and governance modules.
In modern cloud-native systems — microservices, serverless functions, APIs, data services — identity and access control are mission-critical. A role-based, scalable, cloud-native IAM system is more than a security checkbox — it’s the governance fabric that enables agility, safety, compliance, and growth.
If you architect systems of any nontrivial size, here’s what you should do:
- Design your core roles early — don’t wait until you’re too deep.
- Favor least privilege — always start restrictive and open only as needed.
- Use infrastructure-as-code (IaC) for role definitions and policy configuration — version, review, test.
- Log and audit everything — every assignment, every action, every role assumption.
- Iterate and prune roles — avoid role explosion or permission creep.
- Consider conditional access, JIT elevation, and policy logic as your system matures.
- Integrate IAM enforcement into every layer — API gateway, microservices, data, pipelines.
Call to Action:
If you don’t already, pick a small domain in your system (say, user management or a microservice), define roles for it, assign permissions, and implement role checking in code. Audit actions under those role contexts. Then expand role-based IAM step by step until every component in your stack respects centralized IAM.